Search Result.
Case Studies
5
|
Bosch Customized Price Plan
Bosch security systems have quite a good number of resellers through which they sell security devices. For all of their security devices, they have pre-installed SIMs/CDMA’s in them.Now for each customer to have its own login and competitive prices for each operator was a big challenge. They offer the same services for each customer and therefore every customer needs visibility and spends the same amount of money for each device. |
|
|
Bosch: Pioneering Green Engineering with IoT
Large corporations are increasingly under pressure to address environmental concerns while maintaining their business operations. The challenge lies in the perceived trade-off between corporate strategies and environmental responsibility. Many organizations struggle to see the opportunities in green engineering, while others are simply confused by the numerous principles and guidelines that can differ for each industry and organizational department. For instance, electronics engineers can influence the impact of their products by adhering to various design principles such as green engineering, sustainable design, green design, or design-for-environment. These principles share the same basic rules: make it smaller, more reliable, and consume less power. However, engineers must also consider product life cycle, reusability, and how to eliminate toxic chemicals before they can start touting themselves as ‘green engineers’. |
|
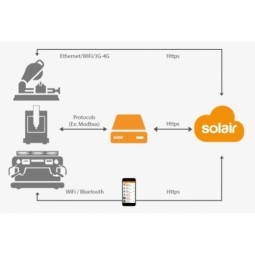 |
Integration of PLC with IoT for Bosch Rexroth
The application arises from the need to monitor and anticipate the problems of one or more machines managed by a PLC. These problems, often resulting from the accumulation over time of small discrepancies, require, when they occur, ex post technical operations maintenance. |
Suppliers
11
_1.jpg) |
Bosch
Bosch is an industry leader in automobile and industrial equipment, as well as consumer goods and building systems. Bosch operates via 440 subsidiaries in 60 countries; its core lines include mobility (auto) systems, from diesel/hybrid drive to steering, starter motors and generators, electronics, and brakes.Year founded: 1886Revenue: $58.7 billion (2014)Portfolio Companies:- Bosch Software Innovations- Rexroth- Deepfield Robotics- Escrypt- ProSyst |
 |
Bosch Automotive Service (Bosch)
Bosch Automotive Service Solutions provides specialized solutions for OEM vehicle service. Bosch provides the aftermarket and workshops worldwide with a complete range of diagnostic and repair shop equipment and a wide range of spare parts for passenger cars and commercial vehicles. |
 |
Bosch IoT Suite (Bosch)
Bosch IoT Suite is the open-source-based Bosch software platform for IoT solutions. Today, it connects more than 10 million sensors, devices, and machines with their users and enterprise systems. |

